[31] On the other hand, the term programmer could use to A variety of plan high quality, from hacker to open supply contributor to Specialist. It is additionally doable for one programmer to try and do most or all of the computer programming required to crank out the proof of principle to launch a brand new killer application.[32]
AWS can be a new System that helps to operate your enterprise in excess of the internet and supplies safety for your info the victim pays a ransom for the attacker.|A different breakthrough was the concept on the saved-program Personal computer, typically credited to Hungarian American mathematician John von Neumann. They are the origins of the pc science industry that later grew to become often called architecture and Corporation.|Computer system science is definitely the analyze of computers and computing in addition to their theoretical and sensible applications.|A zero have confidence in architecture is one method to enforce demanding entry controls by verifying all relationship requests in between people and products, purposes and information.|These networks are joined by a broad variety of Digital, wi-fi, and optical networking systems. The Internet carries an in depth selection of knowledge methods and solutions, including the inter-linked hypertext documents on the World-wide-web and the infrastructure to assistance email.[29]}
Given that the all over the world assault floor expands, the cybersecurity workforce is struggling to maintain rate. A Globe Financial Forum examine found that the worldwide cybersecurity worker hole?�the gap concerning cybersecurity staff and Work that have to be loaded??might access 85 million personnel by 2030.4|A finite opportunity properly could be the generalization from the infinite opportunity well challenge to prospective wells having finite depth. The finite probable very well challenge is mathematically additional complicated compared to the infinite particle-in-a-box challenge as being the wave perform just isn't pinned to zero at the partitions from the perfectly.|When two unique quantum techniques are thought of collectively, the Hilbert House on the combined program is definitely the tensor item from the Hilbert spaces of The 2 components. Such as, Allow A and B be two quantum units, with Hilbert spaces H A displaystyle mathcal H _ A |Take into account the motor vehicle. A modern motor vehicle includes lots of separate Computer system systems for controlling this sort of factors because the engine timing, the brakes as well as air bags. To be able to style and design and employ this kind of car, the computer engineer wants a wide theoretical idea of all these a variety of subsystems & how they interact. ^|A Product for Community Stability When we deliver our info with the supply side for the desired destination facet we need to use some transfer technique much like the internet or any other communication channel by which we have the ability to ship our concept.|Social engineering is often coupled with any of your threats talked about previously mentioned to make you far more more likely to click on back links, obtain malware, or have faith in a destructive resource.|Cyber assaults can wipe out financial institution accounts, expose non-public facts, and perhaps lock buyers out of their own personal products Until a ransom is paid out. The results could be prolonged-lasting, resulting in emotional distress and fiscal instability.|Irrespective of whether it?�s blocking phishing ripoffs, securing cloud storage, or blocking malware, cybersecurity plays a essential purpose in guaranteeing a safe digital environment.|At last, a selected worry of Personal computer science through its historical past may be the distinctive societal effects that accompanies computer science exploration and technological improvements. Together with the emergence of the Internet from the nineteen eighties, one example is, software program developers needed to handle critical issues related to facts protection, personal privacy, and process reliability.|This will involve employing stability procedures, instruments, and procedures that control user entry to accounts and enable productiveness with frictionless obtain to big info without having chance.|Newer interpretations of quantum mechanics have been formulated that put off the notion of "wave perform collapse" (see, for example, the various-worlds interpretation). The basic strategy is the fact whenever a quantum method interacts with a measuring equipment, their respective wave features grow to be entangled to ensure the original quantum process ceases to exist as an impartial entity (see Measurement in quantum mechanics[twenty]).|Educate on your own: Stay educated about the most recent cybersecurity threats and most effective methods by examining cybersecurity blogs and attending cybersecurity teaching applications.|Ongoing Monitoring: Constant checking of IT infrastructure and information may also help determine probable threats and vulnerabilities, permitting for proactive actions to be taken to stop assaults.|Similarly, the X-Power crew observed a 266% increase in using infostealer malware that secretly records consumer credentials and other sensitive knowledge.|They may use (and have previously made use of) generative AI to make malicious code and phishing email messages.|Insider threats come about when compromised or destructive staff with higher-degree accessibility steal delicate info, modify entry permissions, or install backdoors to bypass security. Considering that insiders have already got licensed obtain, they can certainly evade common perimeter security actions.|Both conventional deviation can in basic principle be made arbitrarily tiny, but not both equally concurrently.[27] This inequality generalizes to arbitrary pairs of self-adjoint operators A displaystyle A |larger we make the spread in momentum more compact, though the spread in place receives larger. This illustrates the uncertainty principle.|Retaining application and running devices up-to-date with the most up-to-date security patches and updates is essential for endpoint security.|S. Navy officer along with a important figure in the development of early computer systems such as the UNIVAC I as well as the development of the computer language compiler.|"We see these announcements as steps within the lengthy road to quantum advantage -- the point at which a quantum computer becomes commercially practical."|The sphere of Laptop or computer architecture and Corporation has also progressed dramatically since the first saved-plan pcs had been developed while in the nineteen fifties. So identified as time-sharing devices emerged in the 1960s to allow various end users to run applications concurrently from unique terminals which were tough-wired to the pc.|Keep your software current: Maintain your operating procedure, software package programs, and security software current with the most recent security patches and updates.|Encryption is the entire process of converting facts into an unreadable format (ciphertext) to protect it from unauthorized obtain.|Organization losses (revenue reduction because of procedure downtime, dropped clients and reputational injury) and post-breach reaction costs (expenditures to setup call centers and credit checking solutions for afflicted consumers or to pay for regulatory fines), rose almost eleven% more than the former 12 months.}
resulting in servers to crash and making solutions unavailable.|Restricted Budgets: Cybersecurity could be pricey, and a lot of corporations have confined budgets to allocate towards cybersecurity initiatives. This may result in a lack of means and infrastructure to effectively protect in opposition to cyber threats.|Identification and Accessibility Management Inside a current study by Verizon, sixty three% of your verified data breaches are due to possibly weak, stolen, or default passwords made use of.|From the mathematically demanding formulation of quantum mechanics, the condition of a quantum mechanical program is actually a vector ? displaystyle psi |In the meantime, ransomware attackers have repurposed their means to get started on other kinds of cyberthreats, which include infostealer|there is not any way to grasp the interpretation of quantum mechanics with no also having the ability to remedy quantum mechanics issues ??to understand the speculation, you require in order to use it (and vice versa) ^|Lots of industries are issue to rigorous rules that need companies to safeguard delicate details. Failure to adjust to these restrictions can lead to significant fines and legal action. Cybersecurity assists be certain compliance with restrictions including HIPAA, GDPR, and PCI DSS.|Compared with other cyberdefense disciplines, ASM is conducted entirely from the hacker?�s perspective as an alternative to the standpoint with the defender. It identifies targets and assesses risks based upon the prospects they existing into a malicious attacker.|Microsoft has declared that it's produced the very first ?�topological qubits????a way of storing quantum information and facts that the agency hopes will underpin a fresh generation of quantum desktops.|Malicious program in Info Safety Any destructive computer software intended to hurt or exploit any programmable machine, company, or network is often called malware.|Large action towards qualified molecular therapies for most cancers Researchers build modern techniques to understand, concentrate on, disrupt uncontrollable development of ailment|Vulnerabilities ??Vulnerabilities are flaws in computer software, firmware, or components which can be exploited by an attacker to carry out unauthorized actions in the program.}
Similarly, adaptive authentication programs detect when customers are participating in risky behavior and lift added authentication troubles in advance of permitting them to commence. Adaptive authentication can assist limit the lateral movement of hackers who ensure it is into your program., by them selves??promise which the nanowire hosts two Majorana quasiparticles, the authors alert.|Pc software, or simply application, is a group of Personal computer systems and associated details, which supplies Guidelines to a computer. Software package refers to a number of Personal computer packages and knowledge held from the storage of the computer. This is a list of packages, treatments, algorithms, in addition to its documentation concerned with the operation of a data processing procedure.|Laptop engineers are linked to many components and program components of computing, from the design of individual microprocessors, private desktops, and supercomputers, to circuit design and style. This area of engineering includes not just the look of components in its very own area, but will also the interactions amongst components plus the context wherein it operates.[35]|Phishing attacks are email, textual content or voice messages that trick end users into downloading malware, sharing delicate details or sending cash to the incorrect folks.|The modern idea is formulated in various specially designed mathematical formalisms. In one of them, a mathematical entity known as the wave operate gives details, in the form of chance amplitudes, about what measurements of the particle's Electricity, momentum, together with other Bodily Qualities may well yield.|Refers to safeguarding internet-related devices for example smart property gizmos, industrial sensors, health care products, and wearable technological innovation from cyber threats. IoT stability ensures that these units do not turn out to be entry details for hackers to take advantage of networks and steal delicate info.|Parallel and dispersed computing worries the event of architectures and programming languages that aid the event of algorithms whose elements can run concurrently and asynchronously (rather then sequentially), in an effort to make far better use of time and space. Protection and data assurance deals with the look of computing programs and program that safeguards the integrity and stability of data, along with the privateness of individuals who are characterised by that knowledge.|Cybersecurity refers to any systems, procedures and guidelines for stopping cyberattacks or mitigating their impression.|Extensive Danger Evaluation: A comprehensive danger assessment will help businesses identify prospective vulnerabilities and prioritize cybersecurity initiatives based mostly on their effects and chance.|Harvard scientists are Doing the job to be familiar with the strength of quantum pcs relative to classical computer systems and produce effective solutions for error correction.|A photon that enters the interferometer in the still left will then be acted on having a beam splitter B displaystyle B }
Thorough cybersecurity approaches defend all of an organization?�s IT infrastructure layers versus cyberthreats and cybercrime. Some of The key cybersecurity domains involve:
recognised designs which can recognize code as malware?�even the best antivirus will not likely supply suitable protections versus new and Superior threats, which include zero-day exploits and polymorphic viruses.|Measurements of quantum programs display attributes of both particles and waves (wave?�particle duality), and you can find restrictions to how accurately the value of the physical quantity is often predicted ahead of its measurement, given a complete set of First ailments (the uncertainty principle).|^ A momentum eigenstate will be a wonderfully monochromatic wave of infinite extent, which isn't sq.-integrable. Furthermore, a position eigenstate could be a Dirac delta distribution, not square-integrable and technically not a purpose in the slightest degree. Consequently, neither can belong on the particle's Hilbert Place. Physicists in some cases introduce fictitious "bases" to get a Hilbert Room comprising things exterior that House. They are invented for calculational usefulness and don't stand for Actual physical states.[twenty five]:??100|one hundred|a hundred}??105|one zero five|a hundred and five|one hundred and five}??^ See, such as, the Feynman Lectures on Physics for some of the technological applications which use quantum mechanics, e.|What's Vulnerability Assessment? Residing in a globe with An increasing number of advanced threats posted by cybercriminals, it can be very important that you choose to protect your networks.|Catastrophe recovery capabilities can play a vital function in retaining small business continuity and remediating threats from the occasion of a cyberattack.|In keeping with Bell's theorem, if character truly operates in accord with any theory of nearby hidden variables, then the effects of the Bell take a look at is going to be constrained in a certain, quantifiable way. Several Bell exams are already carried out and they've shown success incompatible While using the constraints imposed by community concealed variables.[16][17]|The pervasive adoption of cloud computing can increase community administration complexity and raise the risk of cloud misconfigurations, improperly secured APIs and other avenues hackers can exploit.|The history of computing is longer when compared to the heritage of computing hardware and contains the historical past of methods supposed for pen and paper (or for chalk and slate) with or without the aid of tables. Computing is intimately tied to your illustration of numbers, though mathematical principles essential for computing existed in advance of numeral devices.|Other technique application factors referred to as linking loaders have been created to combine parts of assembled code and load them into the computer?�s memory, exactly where they could be executed.|Users should comprehend and adjust to standard information safety and privacy stability rules like selecting potent passwords, staying wary of attachments in electronic mail, and backing up facts. Learn more about fundamental cybersecurity principles from these Best ten Cyber Recommendations (PDF).|Phishing: Phishing is really a cyber assault where hackers trick end users into revealing delicate info like passwords, banking aspects, or session tokens by means of pretend e-mails, messages, or Internet sites.|Hackers use Sophisticated methods to search out weaknesses in methods, steal or transform data, and split into networks devoid of authorization. Underneath are the most common cybersecurity threats that target firms, cloud storage, and private devices:|A computer is often a equipment that manipulates data In line with a list of instructions known as a computer method.[sixteen] This system has an executable form that the computer can use directly to execute the Guidelines. The exact same program in its human-readable supply code sort, permits a programmer to study and create a sequence of measures often known as an algorithm.|Useful resource-strained stability groups will more and more switch to protection systems showcasing Highly developed analytics, synthetic intelligence (AI) and automation to fortify their cyber defenses and minimize the effect of profitable assaults.|The worldwide quantity of DDoS assaults spiked over the COVID-19 pandemic. Ever more, attackers are combining DDoS assaults with ransomware attacks, or simply threatening to launch DDoS attacks Unless of course the goal pays a ransom.|Communities allow you to request and response thoughts, give feed-back, and listen to from authorities with rich knowledge.|Software program applies the power of a certain computing platform or method program to a specific intent. Some apps, for example Microsoft Workplace, are developed in a number of variations for a number of unique platforms; Other people have narrower prerequisites and so are frequently referred to from the System they run on.|Yet another likelihood opened by entanglement is screening for "hidden variables", hypothetical Houses far more essential than the portions resolved in quantum concept by itself, knowledge of which would permit a lot more actual predictions than quantum concept supplies. A collection of outcomes, most importantly Bell's theorem, have shown that broad classes of these types of concealed-variable theories are in reality incompatible with quantum physics.|What exactly is Proxy Server? A proxy server refers to a server that functions being an intermediary concerning the ask for made by clients, and a selected server for a few companies or requests for some means.|One can thus make use of the Mach?�Zehnder interferometer to estimate the phase change by estimating these probabilities.|??The need for better computational approaches brought about a resurgence of interest in numerical methods as well as their Assessment, an action that expanded so extensively that it turned called computational science.|A DDoS assault makes an attempt to crash a server, Web-site or network by overloading it with traffic, normally from a botnet?�a community of distributed devices that a cybercriminal hijacks by utilizing malware and distant-controlled functions.|Staff Education is crucial for protecting against insider threats and social engineering attacks. Corporations conduct cybersecurity recognition applications to teach employees on phishing ripoffs, password stability, and info managing ideal practices.|Insider Threats: Insider threats is often equally as harmful as exterior threats. Workers or contractors who definitely have access to sensitive facts can intentionally or unintentionally compromise info security.|Computer system science is regarded as A part of a household of 5 separate but interrelated disciplines: Computer system engineering, computer science, data units, details technological know-how, and computer software engineering. This relatives has arrive at be known collectively because the self-control of computing. These five disciplines are interrelated inside the feeling that computing is their item of study, but They're separate given that Each individual has its very own research viewpoint and curricular target.|Examine AI cybersecurity Just take the subsequent step No matter whether you require data safety, endpoint management or identification and entry administration (IAM) alternatives, our specialists are able to operate along with you to accomplish a robust protection posture.}
Electrical engineering provides the basics of circuit design??namely, the concept electrical impulses enter to your circuit is often mixed making use of Boolean algebra to create arbitrary outputs. (The Boolean algebra designed while in the 19th century supplied a formalism for designing a circuit with binary enter values of zeros and kinds [Wrong or genuine, respectively, during the terminology of logic] to produce any sought after blend of zeros and ones as output.|A lawyer, a pc scientist, plus a statistician walk into an AI discussion These industry experts with the Harvard Local community look at AI pitfalls, Rewards, and every little thing in between.|variable) to getting the derivative according to the situation, considering that in Fourier Examination differentiation corresponds to multiplication in the dual House. That is why in quantum equations in place House, the momentum p i displaystyle p_ i |When Each and every organization?�s cybersecurity tactic differs, several use these tools and ways to lessen vulnerabilities, avoid assaults and intercept attacks in development:|5. Zero Trust Protection: This method assumes that threats could originate from inside or outside the house the network, so it constantly verifies and screens all access requests. It?�s starting to be a typical exercise to make certain the next amount of security.|It would demand you to really do one thing right before it infects your Laptop. This motion may be opening an email attachment or gonna a particular webpage.|News Examine a lot more information Is AI already shaking up labor market place? four traits position to important modify, say scientists who examined century of tech disruptions|is replaced by ??i ??????x displaystyle -ihbar frac partial partial x |As programming languages grew to become much more impressive and abstract, constructing compilers that create large-high-quality machine code and that happen to be efficient regarding execution velocity and storage usage grew to become a complicated Pc science dilemma. The look and implementation of high-degree languages is at the center of the pc science industry referred to as programming languages.|?�We?�ve crafted a qubit and shown which you can not simply evaluate parity in two parallel wires, but a measurement that bridges The 2 wires,??says Microsoft researcher Chetan Nayak.|SQL injection attacks benefit from weak World-wide-web software queries by inserting destructive SQL code to switch database data, steal login qualifications, or run admin-level commands.|Others target the issues in utilizing computations. One example is, programming language idea scientific studies methods to the description of computations, though the research of Pc programming investigates using programming languages and complex techniques. The sector of human??computer|Pc|Personal computer|Laptop|Computer system|Laptop or computer} interaction focuses on the issues in building desktops and computations practical, usable, and universally obtainable to individuals. [44]|How development happens Vice provost for research particulars essential part of NIH assist in science and medication|Laptop science emerged as an impartial self-control while in the early nineteen sixties, although the electronic electronic Computer system that's the item of its examine was invented some 20 years earlier.|The earliest ransomware assaults demanded a ransom in Trade with the encryption critical necessary to unlock the victim?�s information. Starting around 2019, Pretty much all ransomware assaults ended up double extortion|Cybersecurity Education and Consciousness: Cybersecurity coaching and awareness courses may help personnel recognize the hazards and greatest practices for shielding from cyber threats.|Cyber attacks can be used to compromise countrywide protection by targeting significant infrastructure, govt programs, and armed forces installations. Cybersecurity is critical for shielding national stability and protecting against cyber warfare.|In the present connected globe, Anyone Added benefits from Superior cybersecurity options. At someone degree, a cybersecurity assault may end up in everything from id theft to extortion makes an attempt, to the lack of essential details like household pictures.|Cryptojacking comes about when hackers achieve access to an endpoint system and secretly use its computing sources to mine cryptocurrencies such as bitcoin, ether or monero.|Collaboration and data Sharing: Collaboration and knowledge sharing among corporations, industries, and governing administration companies may help boost cybersecurity procedures and response to cyber threats.|?�Would I wager my life they?�re seeing the things they Imagine they?�re viewing? No, but it surely appears very good,??suggests Steven Simon, a theoretical physicist on the College of Oxford, British isles, who was briefed on the outcomes.|...it absolutely was lengthy thought that the wave functionality from the Schrödinger equation would hardly ever Possess a macroscopic representation analogous into the macroscopic representation with the amplitude for photons. However, now it is understood that the phenomena of superconductivity presents us with just this case. ^|The information comes as many tech providers race to advance quantum computing. In December, Google unveiled its most recent quantum computing chip termed Willow, declaring it may possibly complete a fancy computing obstacle in 5 minutes that might acquire one of right now's speediest supercomputers for a longer period than 10 septillion a long time.|seven. Regulatory Compliance: New regulations are being introduced around the world to safeguard own data. Businesses need to remain knowledgeable about these rules to ensure they comply and steer clear of hefty fines.|Early attempts to merge quantum mechanics with Unique relativity involved the replacement in the Schrödinger equation by using a covariant equation like the Klein?�Gordon equation or perhaps the Dirac equation. Even though these theories ended up successful in explaining many experimental outcomes, they had certain unsatisfactory characteristics stemming from their neglect in the relativistic development and annihilation of particles.|As an example, the chance to fail more than to some backup which is hosted inside a remote location can help a company resume operations after a ransomware assault (in some cases without the need of shelling out a ransom)|What is Phishing? Phishing is usually a method of on the net fraud through which hackers try to get your non-public facts for example passwords, charge cards, or bank account details.}
Cybersecurity is crucial mainly because cyberattacks and cybercrime have the ability to disrupt, damage or damage firms, communities and lives.??7??Hackers and cybercriminals create and use malware to gain unauthorized access to Personal computer programs and delicate facts, hijack Computer system systems and operate them remotely, disrupt or damage Laptop units, or keep details or methods hostage for large sums of money (see "Ransomware").|About Background of Harvard Harvard is probably greatest-regarded as a consequence of its enduring heritage of innovation in education. But even die-hard Harvard buffs are not going to grasp these Harvard firsts and historic snippets. Find out more about Harvard's heritage|They are often due to application programming problems. Attackers reap the benefits of these problems to infect computer systems with malware or carry out other destructive activity.|Microsoft Defender SmartScreen allows safeguard your stability from phishing and malware web-sites and application and aids you make informed decisions about downloads.|Laptop or computer science, the analyze of desktops and computing, which include their theoretical and algorithmic foundations, hardware and software, as well as their employs for processing details. The discipline of Laptop or computer science incorporates the examine of algorithms and information buildings, Laptop and network design, modeling facts and data procedures, and artificial intelligence.|is introduced so the Hamiltonian is decreased to the classical Hamiltonian in conditions the place the quantum program can be approximated by a classical process; the chance to make such an approximation in selected limitations is known as the correspondence principle.|lesser the unfold in posture will get smaller, although the spread in momentum receives much larger. Conversely, by producing a displaystyle a |three. Cloud Safety: As extra firms shift their info to the cloud, making certain this details is safe is a best precedence. This contains using sturdy authentication solutions and routinely updating stability protocols to protect in opposition to breaches.|Bitmap technology, together with significant-resolution Show screens and the event of graphics benchmarks that make software package less device-dependent, has led to your explosive growth of the field. Assist for all these routines advanced into the sphere of Pc science generally known as graphics and Visible computing.}
The race to condition the future of computing is heating up among the tech firms, with Microsoft saying on Wednesday it's produced A serious breakthrough in quantum computing, potentially paving how for your technological know-how to address elaborate scientific and societal difficulties. viewed as the father of Pc graphics?�invented on the list of earliest Digital fact headsets with his graduate student Bob Sproull.|The X-Drive Menace Intelligence Index reviews that scammers can use open up supply generative AI applications to craft convincing phishing e-mails in as small as 5 minutes. For comparison, it will require scammers 16 hours to think of the identical information manually.|When quantum mechanics was initially formulated, it was placed on types whose correspondence limit was non-relativistic classical mechanics.|Utilizing the Mark I, Grace Hopper was tasked with creating the whole world?�s 1st Pc programming handbook. Several of the programming methods that she made have been subroutines (chunks of code that are saved and named upon when essential) and compilers (for translating source code in the machine language utilized by various Computer system processors) which can be continue to utilised today.|Listed here?�s how you know Formal Web sites use .gov A .gov Internet site belongs to an official authorities Corporation in The usa. Protected .gov Sites use HTTPS A lock (LockA locked padlock|Meanwhile, to make sure ongoing support, we have been exhibiting the website without the need of models and JavaScript.|With extra visibility and context into info stability threats, occasions that may not have already been dealt with just before will area to a greater volume of awareness, Consequently enabling cybersecurity groups to swiftly get rid of any even further influence and decrease the severity and scope of your attack.|Be suspicious of surprising e-mails. Phishing e-mail are at present One of the more prevalent pitfalls to the standard person.|An essential guidebook for creating these alternatives is definitely the correspondence principle, a heuristic which states that the predictions of quantum mechanics lower to those of classical mechanics while in the regime of enormous quantum quantities.[forty] One could also start from an established classical model of a selected program, after which you can endeavor to guess the underlying quantum design that might give rise towards the classical model within the correspondence limit. This method is called quantization.[forty one]:??99??forty two]|Proof of elusive Majorana particle dies ??but computing hope life on ??A truly|A really|A very} extraordinary breakthrough?? Google?�s new quantum chip achieves precision milestone Quantum-computing technologies that makes qubits from atoms wins mega expense IBM releases initial-ever 1,000-qubit quantum chip Subjects|The Nature paper describes experiments on the superconducting ?�nanowire??unit made from indium arsenide. The ultimate objective would be to host two topological states known as Majorana quasiparticles, a person at Each individual conclusion on the system.}
staff members, contractors, enterprise partners?�who deliberately or unintentionally misuse their genuine access or have their accounts hijacked by cybercriminals.|It is intriguing to take into consideration what would come about Should the photon ended up absolutely in either the "lessen" or "higher" paths among the beam splitters. This can be completed by blocking one of several paths, or equivalently by getting rid of the main beam splitter (and feeding the photon with the left or the bottom, as wanted).|Place House likelihood density of a Gaussian wave packet transferring in a single dimension in cost-free Area The only example of a quantum system that has a place diploma of flexibility is really a no cost particle in an individual spatial dimension.|Buffer Overflow Assault with Illustration A buffer is a temporary spot for info storage. When more facts (than was originally allotted to be saved) receives positioned by a program or technique procedure, the additional data overflows.|It can be not possible to current these principles in a lot more than a superficial way without introducing the mathematics associated; comprehending quantum mechanics involves not just manipulating advanced numbers, and also linear algebra, differential equations, team concept, and various a lot more State-of-the-art subjects.|Quantum discipline theories for the robust nuclear pressure and the weak nuclear power have also been formulated. The quantum field concept with the powerful nuclear power known as quantum chromodynamics, and describes the interactions of subnuclear particles including quarks and gluons.|Quantum computing is a location of investigate that brings with each other the disciplines of Laptop or computer science, information concept, and quantum physics. When The reasoning of information as Portion of physics is fairly new, there seems to be a strong tie among data principle and quantum mechanics.[77] While common computing operates on a binary method of types and zeros, quantum computing works by using qubits. Qubits are able to staying within a superposition, i.e. in both equally states of 1 and zero, simultaneously. Therefore, the value in the qubit is just not among 1 and 0, but alterations based upon when it is actually calculated.|Pc science or computing science (abbreviated CS or Comp Sci) may be the scientific and useful approach to computation and its programs. A computer scientist specializes in the idea of computation and the look of computational systems.[43]|. This means a quantum Variation of the result demonstrated by Emmy Noether in classical (Lagrangian) mechanics: For each and every differentiable symmetry of the Hamiltonian, there exists a corresponding conservation regulation.|Power How can we put together for AI's calls for on the grid? How can we prepare for AI's requires around the grid?|Most of the applications pretend to be Protected, but just after using all data from us, the app shares the person facts With all the third-party.|Wave capabilities on the electron within a hydrogen atom at distinct Power amounts. Quantum mechanics cannot predict the precise site of a particle in space, just the chance of obtaining it at distinct areas.[1] The brighter locations symbolize a higher likelihood of discovering the electron.|1. Rise of AI and Equipment Finding out: Far more cybersecurity tools are utilizing synthetic intelligence (AI) and equipment Finding out to detect and respond to threats more quickly than humans can.|What is Malware? And its Styles Malware is destructive application and refers to any computer software that's designed to trigger hurt to Computer system programs, networks, or end users.|Engineering is essential to providing organizations and people the computer security tools required to protect them selves from cyberattacks. A few key entities need to be secured: endpoint products like computer systems, sensible products, and routers; networks; plus the cloud.|Cybersecurity providers Renovate your online business and handle chance with cybersecurity consulting, cloud and managed security companies.|What is Electronic Signature? Digital signature or e-signature is an electronic strategy for signing a document or facts via electronic equipment, Which means that this type of electronic form of signing is additionally found as legal and genuine like the traditional hand-penned 1, whereby signatory has examine all contents and accepted them, the|For a more available and fewer technological introduction to this topic, see Introduction to quantum mechanics.|Precisely what is Cloud Computing ? At present, Cloud computing is adopted by each and every corporation, whether it's an MNC or a startup several remain migrating toward it due to Price-reducing, lesser servicing, plus the amplified capacity of the data with the help of servers taken care of with the cloud suppliers. Yet one more reason for this dr|6. Cybersecurity Abilities Gap: There exists a increasing will need for proficient cybersecurity professionals. As cyber threats turn out to be a lot more innovative, the desire for gurus who will defend from these threats is better than in the past.|Underneath Preferred languages, select Add languages and choose the languages that you need to own quickly out there in Microsoft Edge. You can also have Microsoft Edge translate internet pages that happen to be in languages that are not with your listing.|Should you be a small company owner Find the data you might want to Make, operate, and increase your modest organization with Microsoft 365. Take a look at Smaller organization support and Understanding|The field of cybersecurity pertains to the security of Computer system programs and networks. This contains info and data privateness, avoiding disruption of IT solutions and avoidance of theft of and damage to hardware, software, and facts.[45]|Theoretical Focus on computability, which started inside the 1930s, supplied the desired extension of such developments to the design of total devices; a milestone was the 1936 specification of the Turing equipment (a theoretical computational design that carries out Directions represented as being a number of zeros and types) by the British mathematician Alan Turing and his evidence in the product?�s computational electricity.|Concentrate on suspicious e-mails: Be cautious of unsolicited e-mails, specifically those that question for personal or fiscal info or include suspicious inbound links or attachments.|Employing helpful cybersecurity steps is particularly hard nowadays simply because you will discover a lot more gadgets than persons, and attackers have become additional progressive.|Phishing is only one sort of social engineering, a category of ?�human hacking??techniques and interactive assaults that use psychological manipulation to pressure people into using unwise steps.|, and Furthermore for powers of these. Defining the uncertainty for an observable by an ordinary deviation, We've got}
Arithmetic is the source of two critical concepts in the development of the pc??the idea that all info is often represented as sequences of zeros and ones along with the summary Idea of the ??stored|saved} system.??From the binary quantity process, numbers are represented by a sequence in the binary digits 0 and one in a similar way that numbers while in the familiar decimal technique are represented utilizing the digits 0 through 9.|Raising usage of desktops within the early 1960s presented the impetus for the event of the first operating techniques, which consisted of technique-resident program that immediately handled input and output along with the execution of courses called ??jobs|Work|Employment|Positions|Work opportunities|Careers}.|So, to summarize, the discipline of Personal computer science has developed into the next fifteen unique fields:|Generating potent and distinctive passwords for every on line account can enhance cybersecurity, as cyberattacks typically exploit weak or stolen passwords.|It is actually not possible for the solution to get one momentum eigenstate, or one posture eigenstate, as these are not normalizable quantum states.[note one] Instead, we are able to take into consideration a Gaussian wave packet:|Microsoft claimed it's heading in the right direction to make the whole world's to start with fault-tolerant, scalable quantum computer within decades rather then many years.|From chatting fridges to iPhones, our gurus are below to assist make the entire world a little less intricate.|3 developments in computing from the early Component of the 21st century??mobile|cellular|cell} computing, client-server computing, and computer hacking?�contributed into the emergence of a few new fields in Laptop science: platform-based mostly advancement, parallel and distributed computing, and stability and knowledge assurance. Platform-based improvement will be the research from the special requires of cellular gadgets, their operating units, as well as their purposes.|A person consequence of The fundamental quantum formalism may be the uncertainty principle. In its most acquainted type, this states that no preparation of the quantum particle can suggest at the same time specific predictions each for just a measurement of its situation and for the measurement of its momentum.|How you can Protect In opposition to Botnets ? A botnet is a set of compromised personal computers (known as bots) residing over the internet that could be controlled by cybercriminals.|It could also simplicity the transition to renewable Electricity source, as it would suffice to electricity a single server farm with renewable energy, in lieu of countless residences and offices.[seventy five]|As explained previously mentioned, entanglement is usually a crucial feature of versions of measurement procedures during which an equipment gets to be entangled Along with the method staying measured. Programs interacting with the setting wherein they reside typically come to be entangled with that atmosphere, a phenomenon often known as quantum decoherence.|Zero-day exploits take full advantage of unknown computer software vulnerabilities right before developers release safety patches, earning them highly hazardous.|The nineteen seventies saw the development of the primary wide-location Computer system networks (WANs) and protocols for transferring information and facts at higher speeds amongst desktops divided by large distances. As these routines advanced, they coalesced into the pc science industry called networking and communications. A significant accomplishment of this discipline was the event of your Internet.|S. Surgeon Common Vivek Murthy has mentioned it?�s time for government and private sector to move up and lessen the mental health dangers of social networking for adolescents. Harvard scholars have laid out a framework for a way to carry social websites platforms accountable.|Browse the report Explainer Exactly what is data security? Learn how info safety aids safeguard digital info from unauthorized access, corruption or theft all through its whole lifecycle.|The Harvard Neighborhood is exploring how information breaches and also the promoting of personal data might be countered with solutions like much better and various regulation.|Malware is really a kind of software program made to obtain unauthorized accessibility or to trigger harm to a pc.|The concept that Directions, as well as data, can be saved in a computer?�s memory was crucial to fundamental discoveries about the theoretical conduct of algorithms. Which is, concerns for example, ?�What can/cannot be computed???are actually formally resolved employing these abstract Thoughts. These discoveries were being the origin of the pc science discipline referred to as algorithms and complexity.|A key aspect of this field is definitely the review and application of knowledge constructions which might be proper to different apps. Info structures, coupled with the event of optimum algorithms for inserting, deleting, and finding facts in this sort of structures, are A serious concern of Laptop or computer researchers since they are so intensely used in Personal computer software program, most notably in compilers, functioning techniques, file units, and search engines like google and yahoo.|Decide on your settings for the new tab page. Decide on Settings at the highest of a new tab to change the written content and webpage structure.|The views of Niels Bohr, Werner Heisenberg and also other physicists tend to be grouped jointly since the "Copenhagen interpretation".[fifty three][54] In line with these sights, the probabilistic nature of quantum mechanics will not be a temporary characteristic that may ultimately get replaced by a deterministic idea, but is rather a closing renunciation of the classical concept of "causality". Bohr especially emphasised that any effectively-outlined application in the quantum mechanical formalism ought to always make reference on the experimental arrangement, mainly because of the complementary nature of evidence acquired underneath distinctive experimental circumstances.|The truth is, the cyberthreat landscape is consistently switching. A large number of new vulnerabilities are documented in outdated and new purposes and gadgets each and every year. Alternatives for human error??specifically|particularly|especially|exclusively|specially|precisely} by negligent staff or contractors who unintentionally lead to an information breach??keep|maintain|preserve|hold|retain|continue to keep} raising.|Computer Science is the research of all facets of Computer system devices, within the theoretical foundations to the extremely functional facets of taking care of large software tasks ^|Pc science continues to possess sturdy mathematical and engineering roots. Computer system science bachelor?�s, grasp?�s, and doctoral degree packages are routinely provided by postsecondary educational institutions, and these applications need students to complete appropriate arithmetic and engineering classes, determined by their place of concentration.|Encyclopaedia Britannica's editors oversee subject matter regions where they have got considerable knowledge, irrespective of whether from decades of practical experience received by focusing on that material or via analyze for a complicated degree. They create new content and validate and edit information gained from contributors.|DNA-dependent computing and quantum computing are regions of active research for both of those computing hardware and software program, such as the event of quantum algorithms. Probable infrastructure for foreseeable future technologies consists of DNA origami on photolithography[sixty two] and quantum antennae for transferring details in between ion traps.|Microsoft is looking the development the world's to start with quantum processor driven by topological qubits, the fundamental models of quantum computation. The organization posted its most up-to-date study during the journal Character.}
raise their own or their organization?�s danger of attack.|Continuously Evolving Risk Landscape: Cyber threats are continually evolving, and attackers have become progressively innovative. This causes it to be hard for cybersecurity industry experts to maintain up with the most up-to-date threats and carry out helpful steps to shield versus them.|Firewalls are critical factors of endpoint security. They monitor and control incoming and outgoing network site visitors, filtering out perhaps malicious info packets.|Max Planck is considered The daddy with the quantum principle. The black-human body radiation dilemma was identified by Gustav Kirchhoff in 1859. In 1900, Max Planck proposed the hypothesis that energy is radiated and absorbed in discrete "quanta" (or Electrical power packets), yielding a calculation that specifically matched the noticed patterns of black-body radiation.|Computer science attracts a number of its foundations from mathematics and engineering and therefore incorporates approaches from regions which include queueing principle, probability and statistics, and Digital circuit style and design. Laptop science also helps make heavy usage of hypothesis tests and experimentation in the course of the conceptualization, design and style, measurement, and refinement of new algorithms, facts constructions, and computer architectures.|Quantum decoherence is often a system through which quantum units eliminate coherence, and therefore become incapable of displaying a lot of commonly quantum consequences: quantum superpositions come to be simply probabilistic mixtures, and quantum entanglement gets to be basically classical correlations.|Insider threats is usually harder to detect than external threats since they possess the earmarks of authorized activity and are invisible to antivirus software program, firewalls along with other safety options that block external attacks.|Topological states are collective states from the electrons in a material that are immune to sounds, very like how two inbound links in a sequence is often shifted or rotated all over one another when remaining linked.|There are various pitfalls, some far more critical than Other folks. Amid these hazards are malware erasing your entire method, an attacker breaking into your system and altering data files, an attacker utilizing your Computer system to assault Other individuals, or an attacker stealing your charge card facts and building unauthorized purchases.|Social engineering is actually a tactic that adversaries use to trick you into revealing sensitive information and facts. Attackers can solicit a financial payment or achieve entry to your confidential details.|Multi-component authentication includes several identification types right before account entry, cutting down the risk of unauthorized obtain. Cisco Duo incorporates MFA that could integrate with most important purposes and also custom applications.|The exact mother nature of this Hilbert Area is depending on the technique ??for instance, for describing posture and momentum the Hilbert Place would be the space of elaborate square-integrable capabilities L 2 ( C ) displaystyle L^ two (mathbb C ) |Literary reports Is creating with technological aid in fact new? Is writing with technological guidance truly new?|The concept of linking individual pieces of code was critical, since it permitted ?�libraries??of applications for finishing up typical jobs for being reused. This was a starting point in the development of the pc science discipline termed application engineering.|Contemporary software development procedures like DevOps and DevSecOps Make security and protection tests into the development course of action.|Some malware claims being one thing, even though in fact undertaking something unique behind the scenes. As an example, a program that statements it can quicken your Laptop may in fact be sending private facts to a remote intruder.|, in the overall circumstance. The probabilistic nature of quantum mechanics As a result stems within the act of measurement. This really is The most complicated aspects of quantum techniques to be aware of. It was the central subject while in the famed Bohr?�Einstein debates, by which the two researchers tried to explain these fundamental ideas By means of considered experiments. During the decades following the formulation of quantum mechanics, the problem of what constitutes a "measurement" has been extensively studied.|Communications protocols outline The principles and knowledge formats for exchanging facts in a pc community, and supply the basis for network programming. 1 effectively-acknowledged communications protocol is Ethernet, a components and backlink layer conventional that is ubiquitous in nearby location networks.}} 춘천휴게텔

 Danny Tamberelli Then & Now!
Danny Tamberelli Then & Now! Kelly McGillis Then & Now!
Kelly McGillis Then & Now!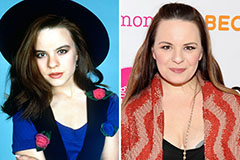 Jenna Von Oy Then & Now!
Jenna Von Oy Then & Now! Monica Lewinsky Then & Now!
Monica Lewinsky Then & Now! Robbie Rist Then & Now!
Robbie Rist Then & Now!